FortiGate VM Trial license not working
Troubleshooting a FortiGate VM Trial License: A Step-by-Step Guide to Resolving the Issue
If you have been having trouble getting a FortiGate VM Trial license to work, then you are not alone. Many users have encountered this issue and have found it difficult to resolve. Fortunately, this article will provide you with the steps necessary to get your VM Trial license working properly. We will discuss the necessary steps for activating and validating your FortiGate VM Trial license as well as troubleshooting any issues that may arise during the process. By following these instructions, you should be able to get your FortiGate VM Trial license up and running in no time.
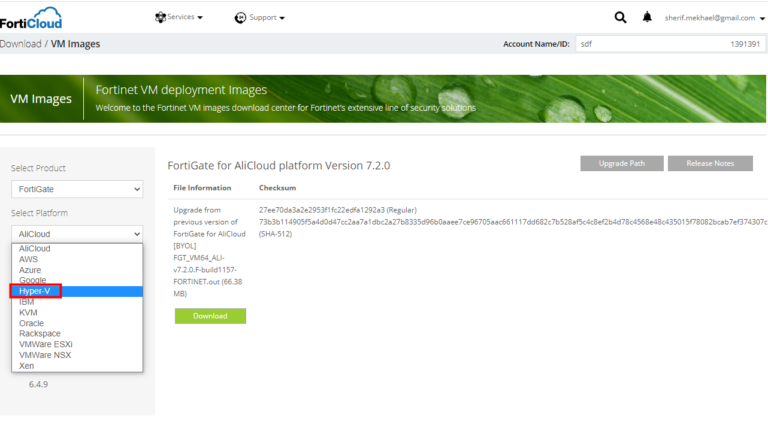
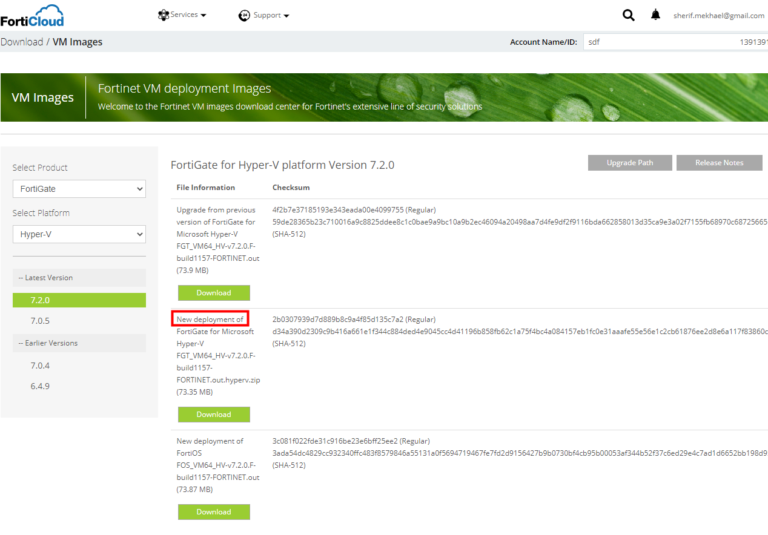
Understanding the FortiGate VM Trial License Limitations
Before troubleshooting, it’s crucial to understand the limitations of the evaluation license. The FortiGate Trial license does not support HTTPS for management, which means that you would have to manage it via HTTP.
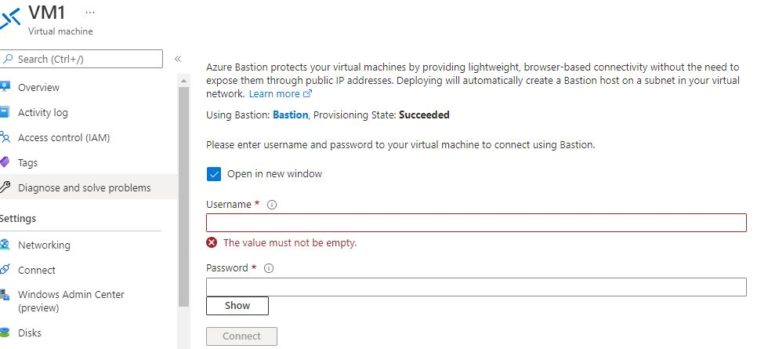
Moreover, when the Fortigate default login is used, which is the admin, no password is required. After pressing enter, the firewall system forces you to set up a new password for better security.
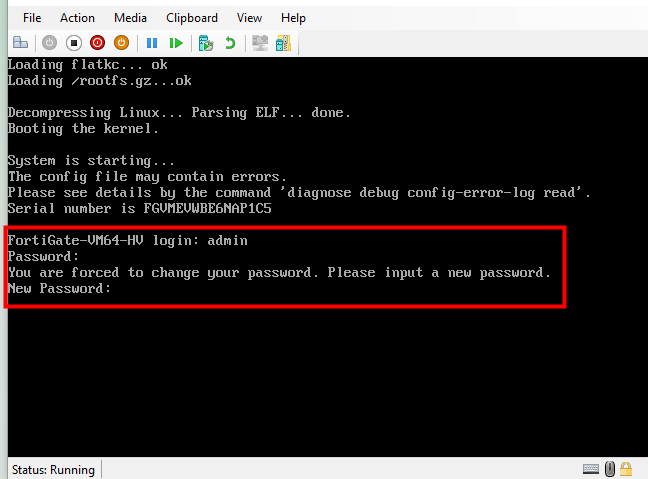
Diagnosis: Identifying the VM License Issue
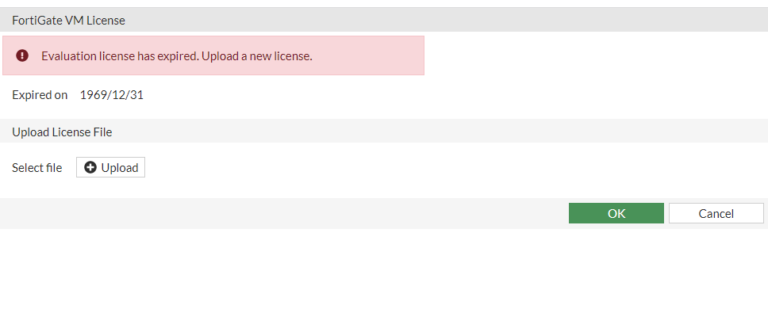
Often, the problem begins with your FortiGate VM trial license not working as expected.
To troubleshoot this, enter #execute factoryreset then type y. This action is aimed at restoring the factory settings and fixing the VM license issue.
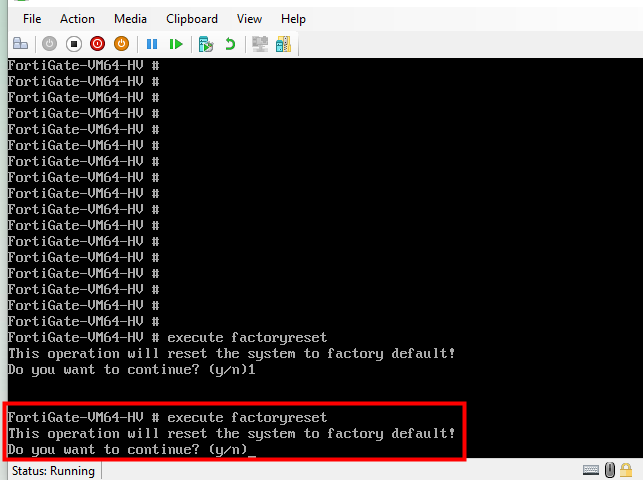
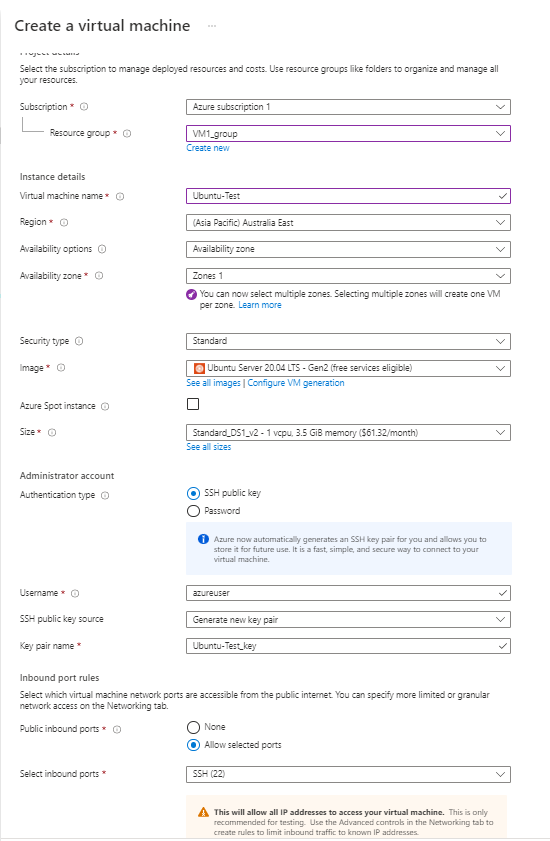
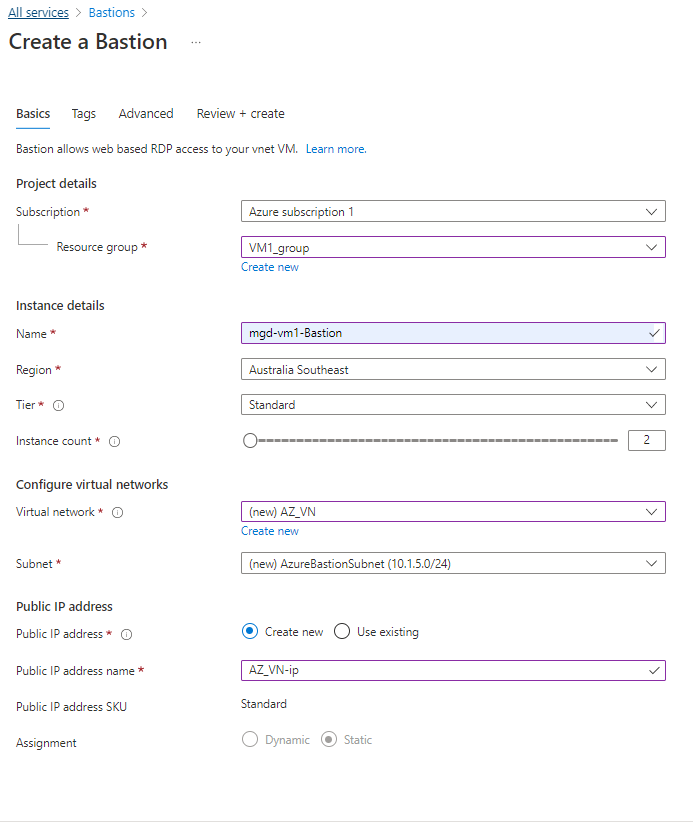
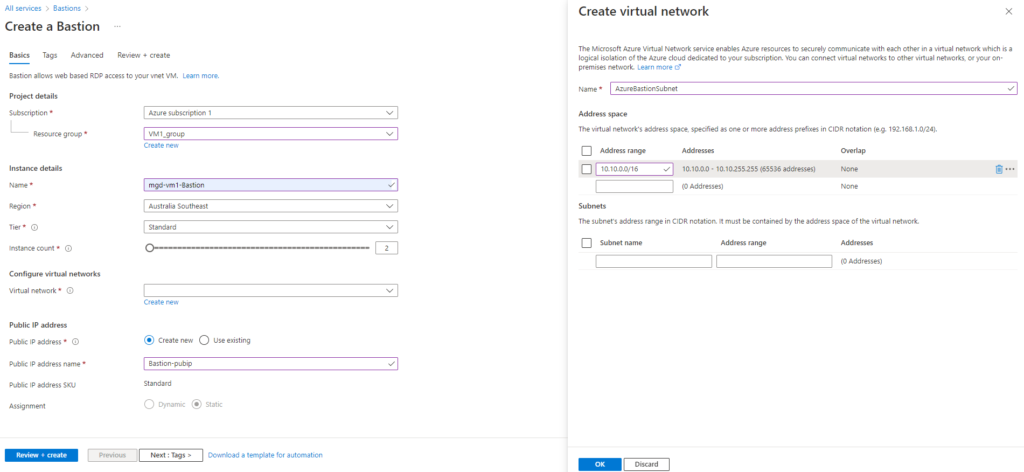
Setting up the initial configuration of a FortiGate Firewall.
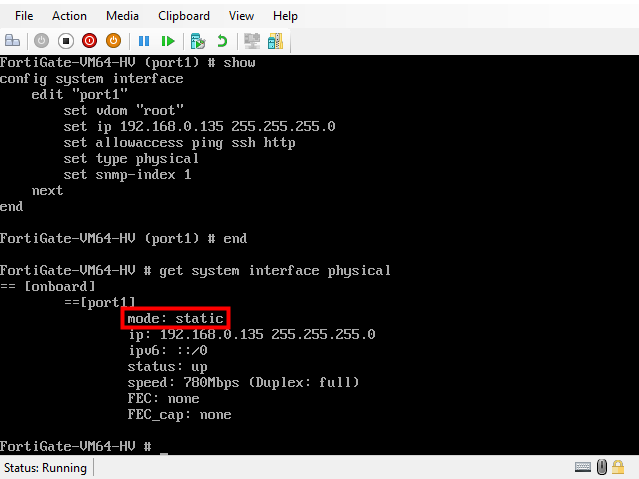
To show the current IP address and the mode
#get system interface physical
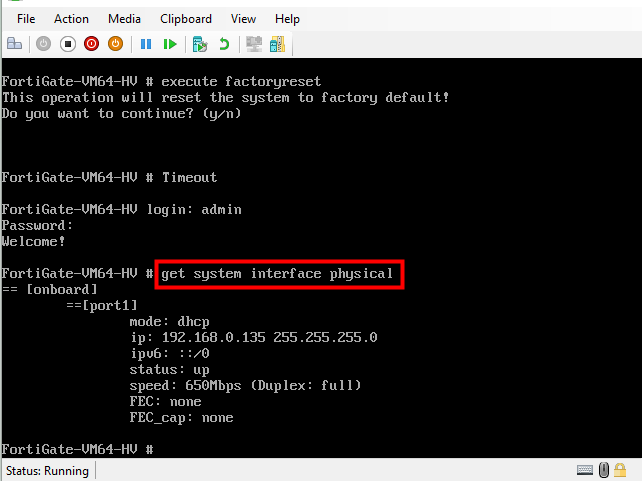
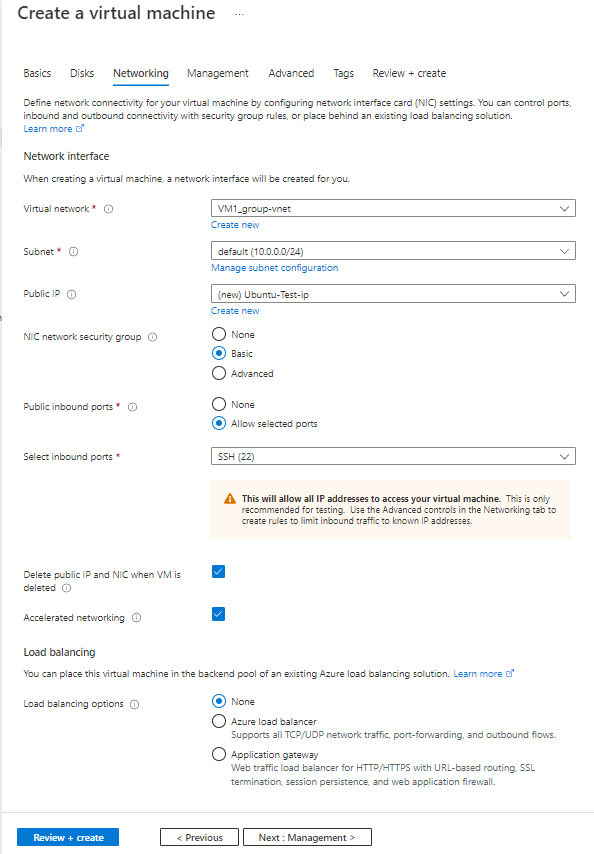
Configuring Network Settings
Next step: switch your network configuration to static and enter the IP address manually. Use the commands below to achieve this:
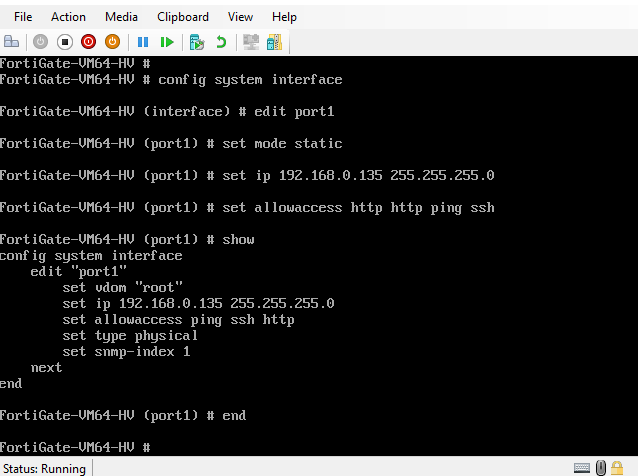
#config system interface
#show
To edit (configure) certain port number
#edit port1
#set mode static
#set ip 192.168.0.135 255.255.255.0
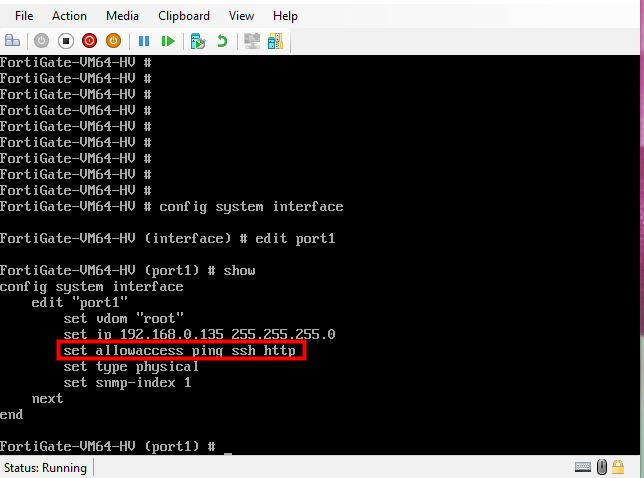
To access the firewall through that port, you must enable HTTP (included with the evaluation license). Upgrading to the full version will give you the added benefit of accessing the firewall via HTTPS and SSH as well.
The command for this is:
#set allowaccess http ssh ping https
Setting up Internet Access and DNS Serve
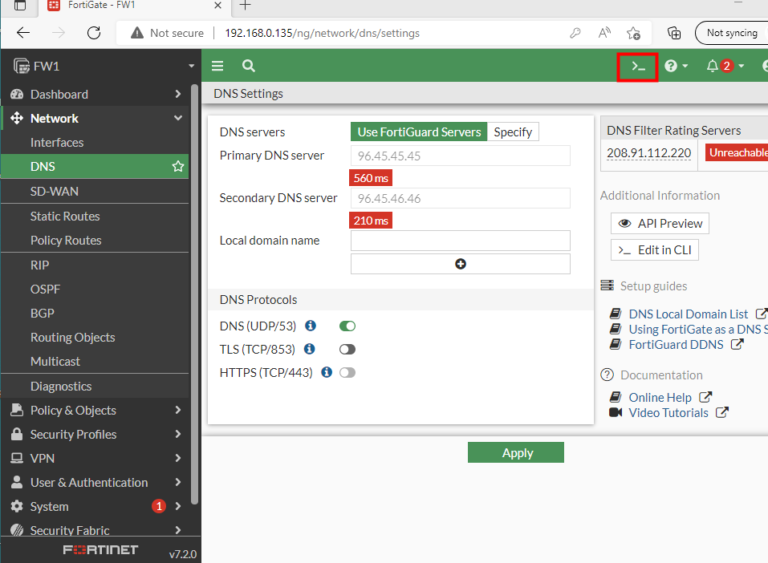
By default, the system utilizes Fortinet’s DNS servers. However, you have the flexibility to modify the DNS settings if required.
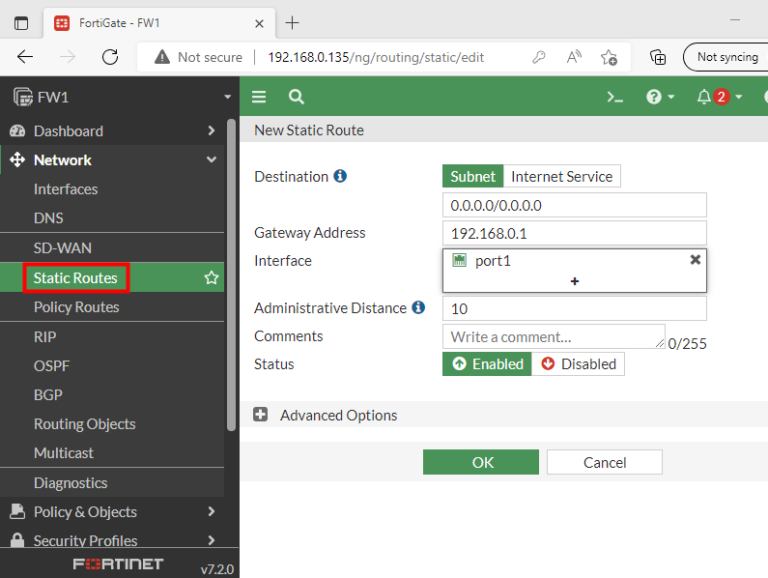
You need to set up a static default route to get an internet access route.
Network > Static Routes
By default, Fortinet‘s DNS servers are being used, but you can alter the DNS settings if desired.
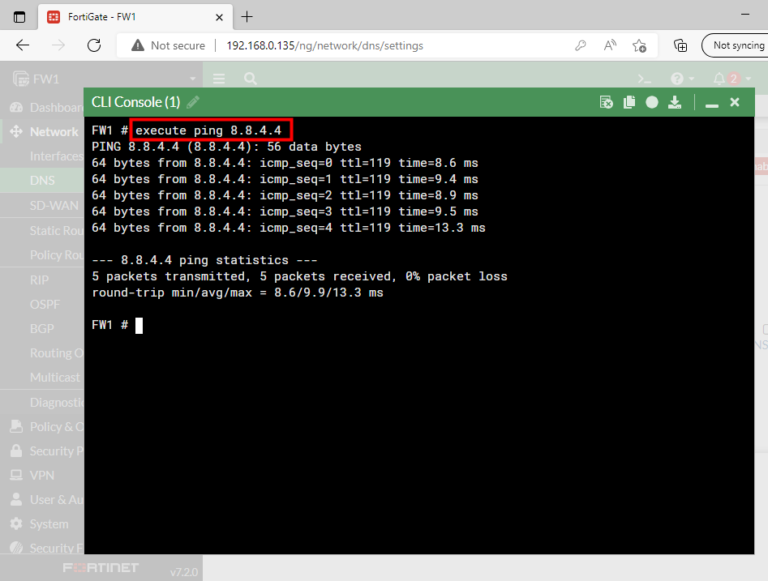
You can launch a new console window from the graphical user interface (GUI).
Concluding thoughts
Finally, it is important to note that a new console window can be launched from the graphical user interface (GUI) for more convenience.
In the end, while the FortiGate VM Trial license has its limitations, understanding and working around these constraints can allow you to explore the robust benefits of FortiGate VM and eventually make an informed decision about upgrading to the full version.